Log in in Plone using your Google Workspace account
WARNING: see the new version of this blog post here, with some improvements for our Plone setup.
We usually need to access clients' Plone sites to do either content management or debugging stuff, and to do so we have our own accounts on those Plone sites. Nevertheless is time consuming to manage all those Plone accounts, save the passwords, remove old co-workers accounts etc.
For some time we are using Google Workspace for our corporate e-mail and documents, so we thought that could be interesting to investigate how to use our Google Workspace accounts to log in into Plone. The process is very easy and can be achieved using 2 addons. This is the procedure I followed:
We have tested this procedure in Plone 5.2 and 6.0b3.
- Install Plone as you would usually do.
- Install pas.plugins.oidc and pas.plugins.memberpropertytogroup in your Plone instance and enable them in Plone. In the first case, you need to install the current version from the main branch on GitHub. In the second case, you will need to install our version until a new version is released or merged in the original repo.
- Go to your Google Cloud Console and create a new Project and name it like "<Your Company> Single Sign On" (this name is an example, use whatever you want).
- Expand the left menu using the burger-menu and go to APIs & Services -> Credentials
- Create a new Credential using the top-bar option and select OAuth client ID. At this point Google may require you to configure an OAuth consent screen
- Set the user type as Internal. This way only users from your Google Workspace organisation will be able to log in using this application.
- Set all other parameters such a custom name, logo and links to the privacy policy.
- In the "Your non-sensitive scopes" option select the following ones:
- .../auth/userinfo.email
- .../auth/userinfo.profile
- openid
- Do not select anything in Your sensitive scopes or Your restricted scopes.
- Select Web application as a type and name it like you want. Set the following url as an Authorized redirect URIs: https://your.plonesite.com/acl_users/oidc/callback. Note that you need to expose your Plone site in case your frontend is Volto, because the user will be redirected to his URL after the login process concludes.
- If you haven't been prompted to configure an OAuth consent screen, go to that option and create a new one using the configuration explained in the 3.2 point.
- Download the generated credentials JSON file, and save it under your Pillow.
- Go to your Plone instance at https://your.plonesite.com/acl_users/oidc/manage_propertiesForm and configure your oidc plugin as follows:
- OIDC/Oauth2 Issuer: https://accounts.google.com
- Client ID: copy the client id stated in the credentials file, it will end with XXXXX.apps.googleusercontent.com
- Client secret: copy the secret from the credentials.file
- Redirect uri: set the folowing url (in one line): https://your.plonesite.com/acl_users/oidc/callback
- Check "Create user / update user properties", "Create authentication __ac ticket", "Create authentication auth_token (volto/restapi) ticket" and "Use PKCE" options.
- Enter the following options in the "Open ID scopes to request to the server" (one per line): profile email openid
- Save the changes
- Go to Plone Control Panel -> Member Property To Group. Here we will configure Plone to let the users coming from your company to be Managers
- Add "email" as a Users Group Property Field
- Add a line like this one in the Mapped Groups option: *domain.com|company|Company|Company Group Description|info@company.com
This will create a group called "Company" in Plone, and will assign all users with an email that ends with domain.com as members of that group
- Go to Plone Control Panel -> Groups and set the Manager role to the group Company
- Logout from Plone and from the ZMI
Now you are ready to test your setup. Just open a new browser and go to https://your.plonesite.com/acl_users/oidc/login You will be redirected to Google to log in, and you will only be allowed to log in using your Google Workspace account. After loging in there successfully you will be redirected back to Plone and you will be a Manager there. Look at the following screenshots.
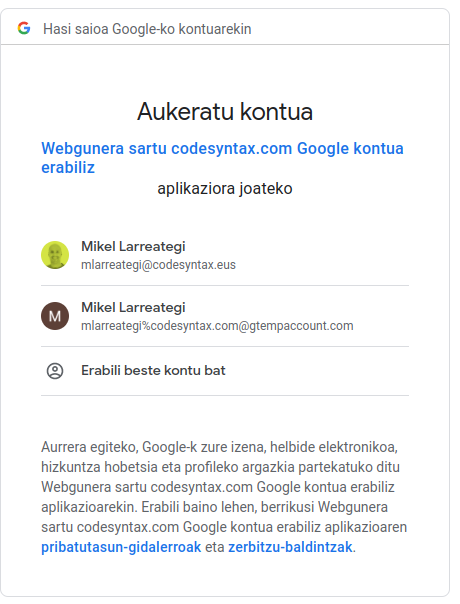
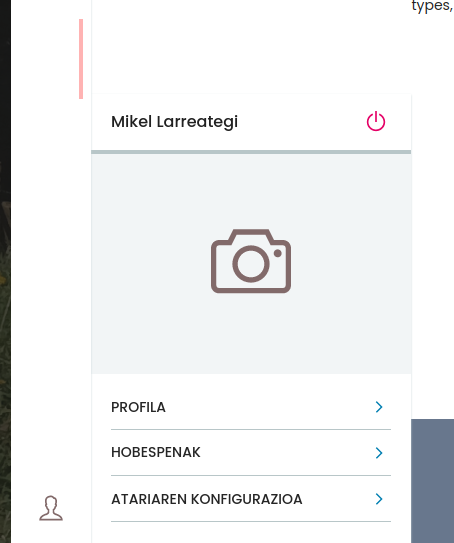
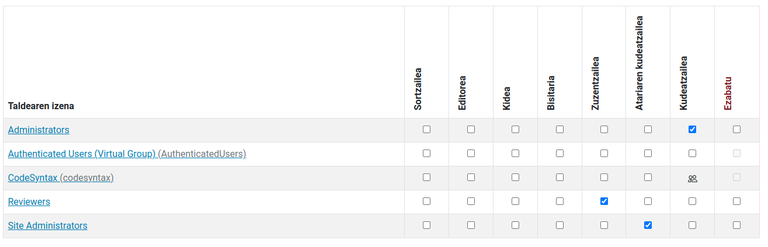
This way you do not need to have extra users and passwords in your site.
This approach has one drawback: right now we are using pas.plugins.memberpropertytogroup to handle the group assignment and thus the permissions. Any user that can change his own email address to your company's e-mail can be upgraded to be Manager. This is a security issue that we need to check further. We are thinking on checking which user profile data comes from Google, and check whether we can use that to identify users.
The setup is built on top of pas.plugins.oidc a plugin by Mauro Amico that we are already using at the EEA to connect with Keycloak and EU Login which offer an Open ID Connect compatible interface. This may also work using the excellent pas.plugins.authomatic because it supports OAuth 2 and Google, but we haven't tested it. The plugin will be updated in the coming weeks by Eau de Web to support environment variable based configuration (it is already available at the EEA fork of the product but not integrated yet in the main repository).
This opens a way to remove all our management users from our Plone sites and use our Google Workspace account to log in there. This way we can use our Google accounts' Multi Factor Authentication configuration, we can easily revoke access to old co-workers, etc. And it is much easier than setting up an LDAP server or configuring an external service like Keycloak.
Credits
We have extracted the configuration reference from this help page on how to configure OpenShift to connect to Google Workspace.
You may be interested in these other articles
Plone Foundation New Members
Oct 14, 2025
CodeSyntax at PLONECONF 2025: Jyväskylä - Finland
Sep 12, 2025
Beethoven Sprint 2025
Jun 20, 2025



